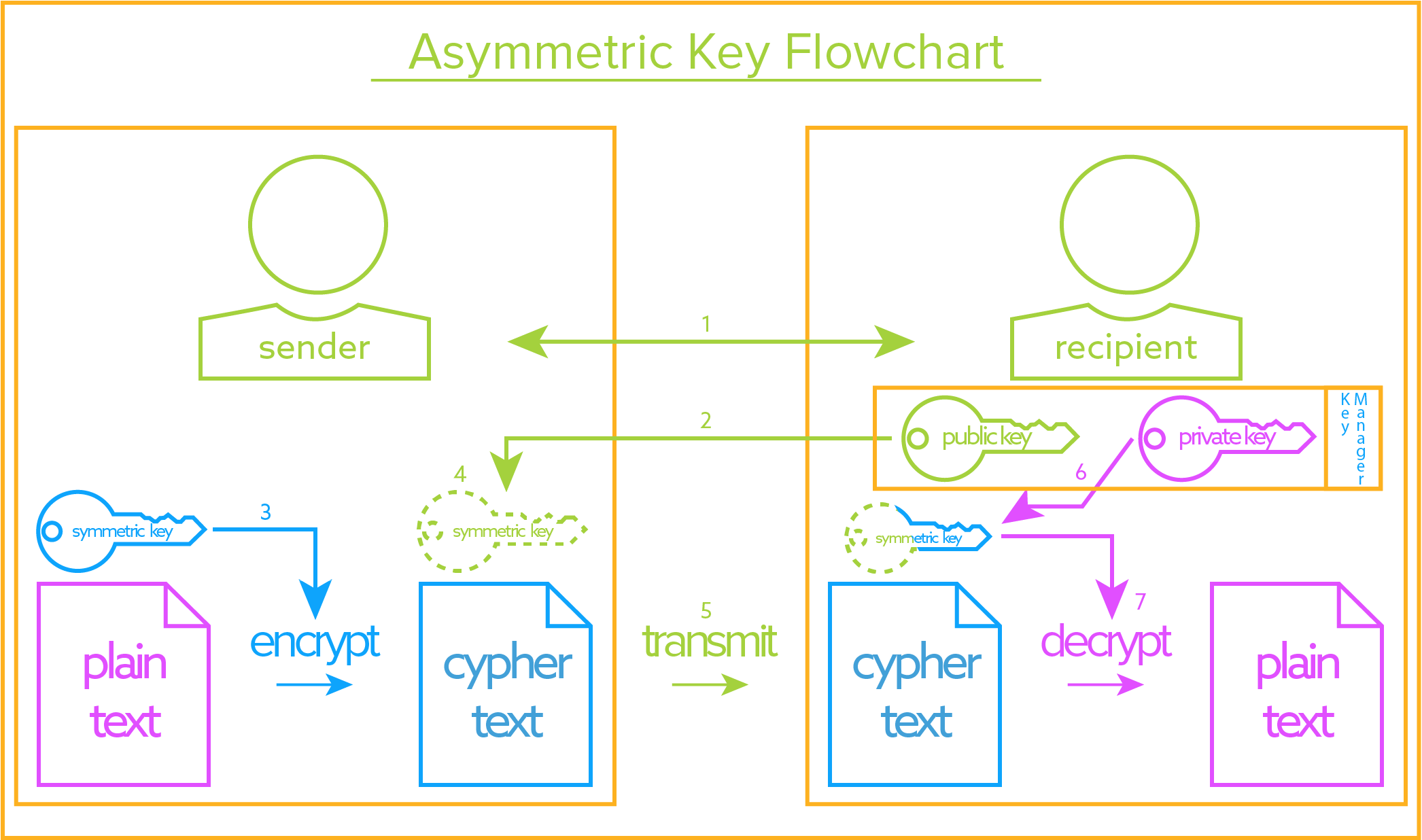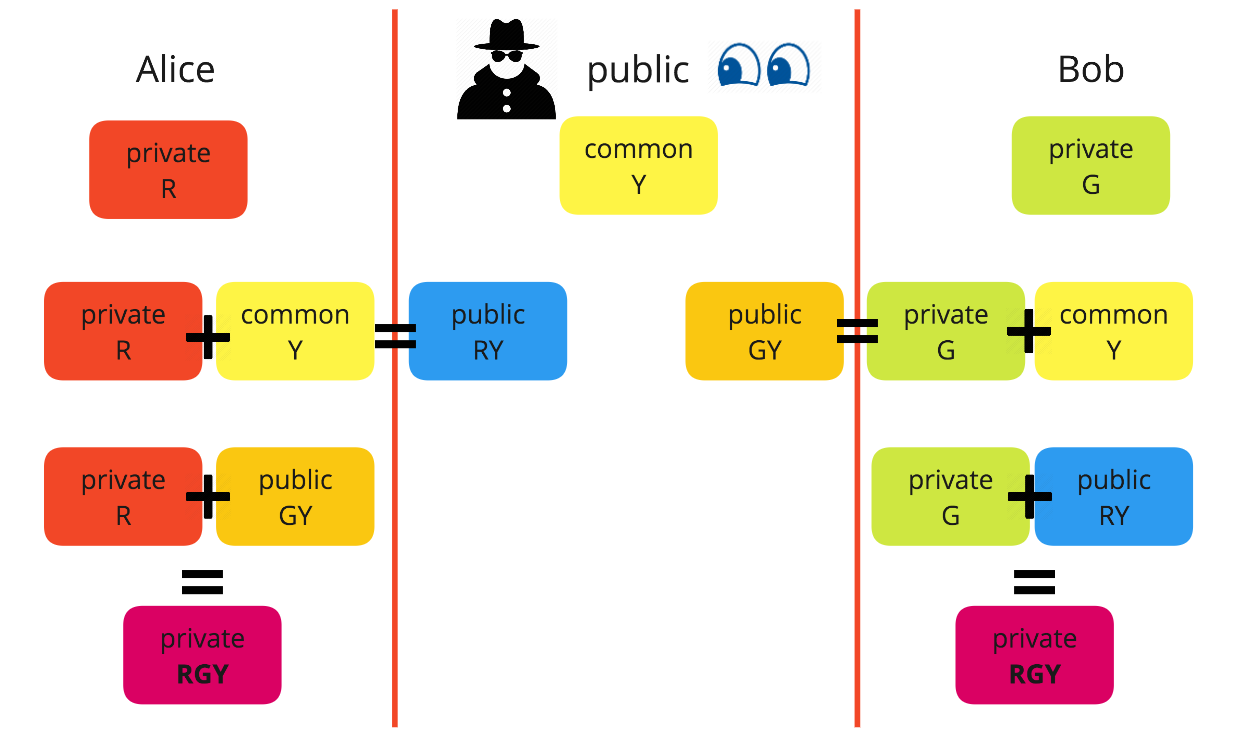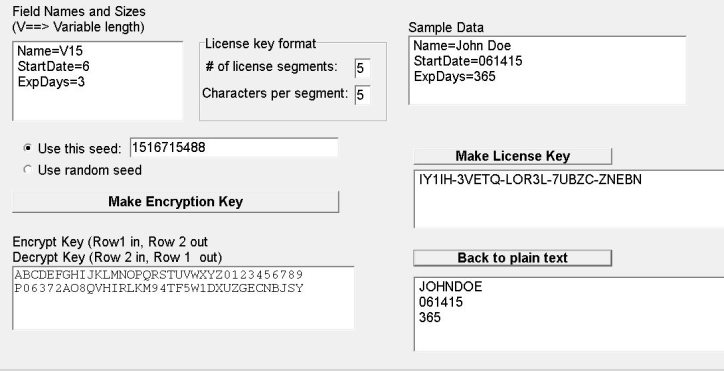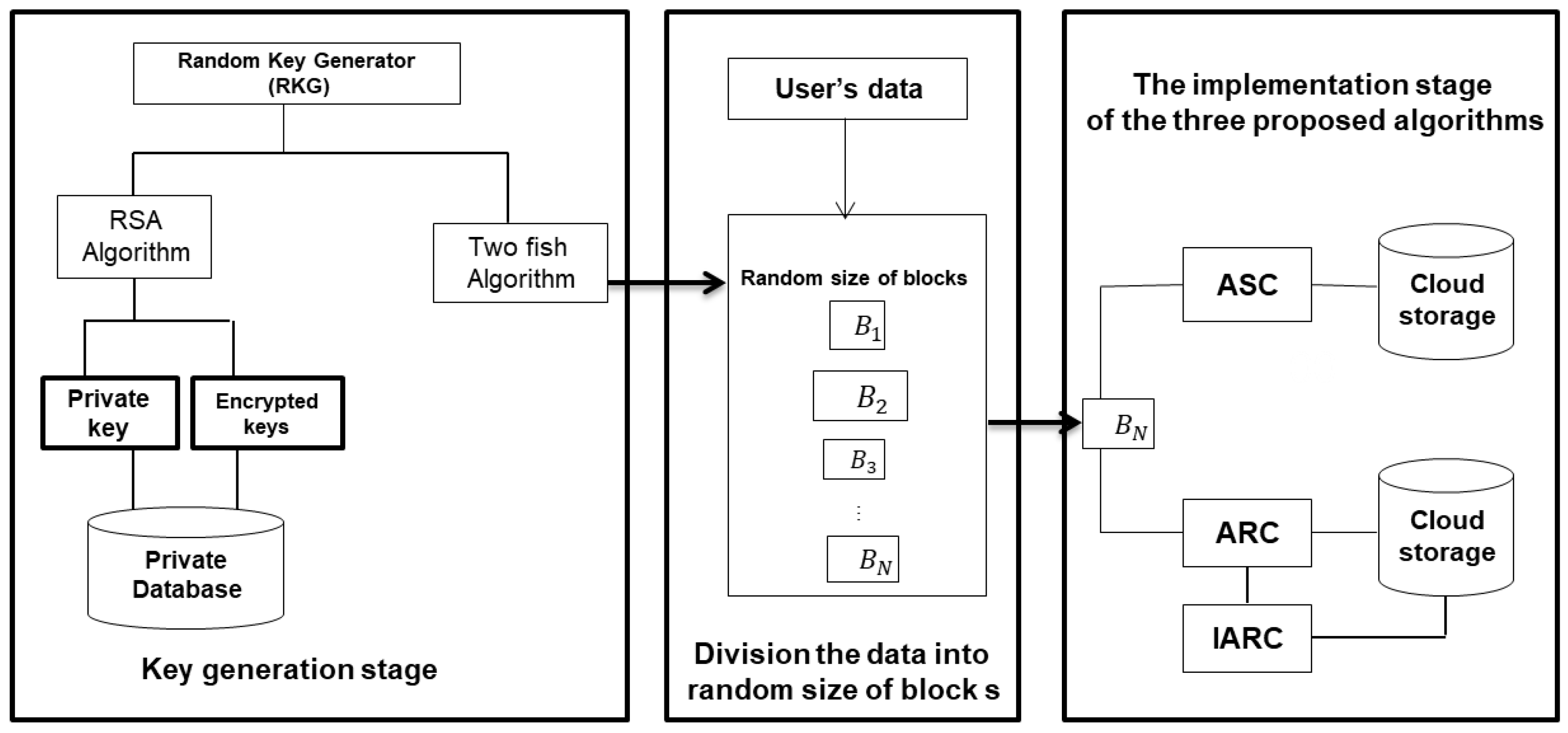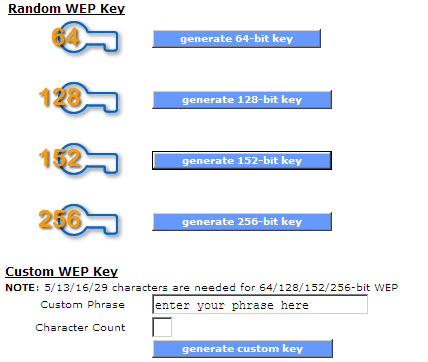
RNG — The Secret of Cryptography. Random Generator Number is the core… | by CuongQuay | Problem Solving Blog | Medium

encryption - How does GRC password generator get 512 bit of secret data? - Cryptography Stack Exchange
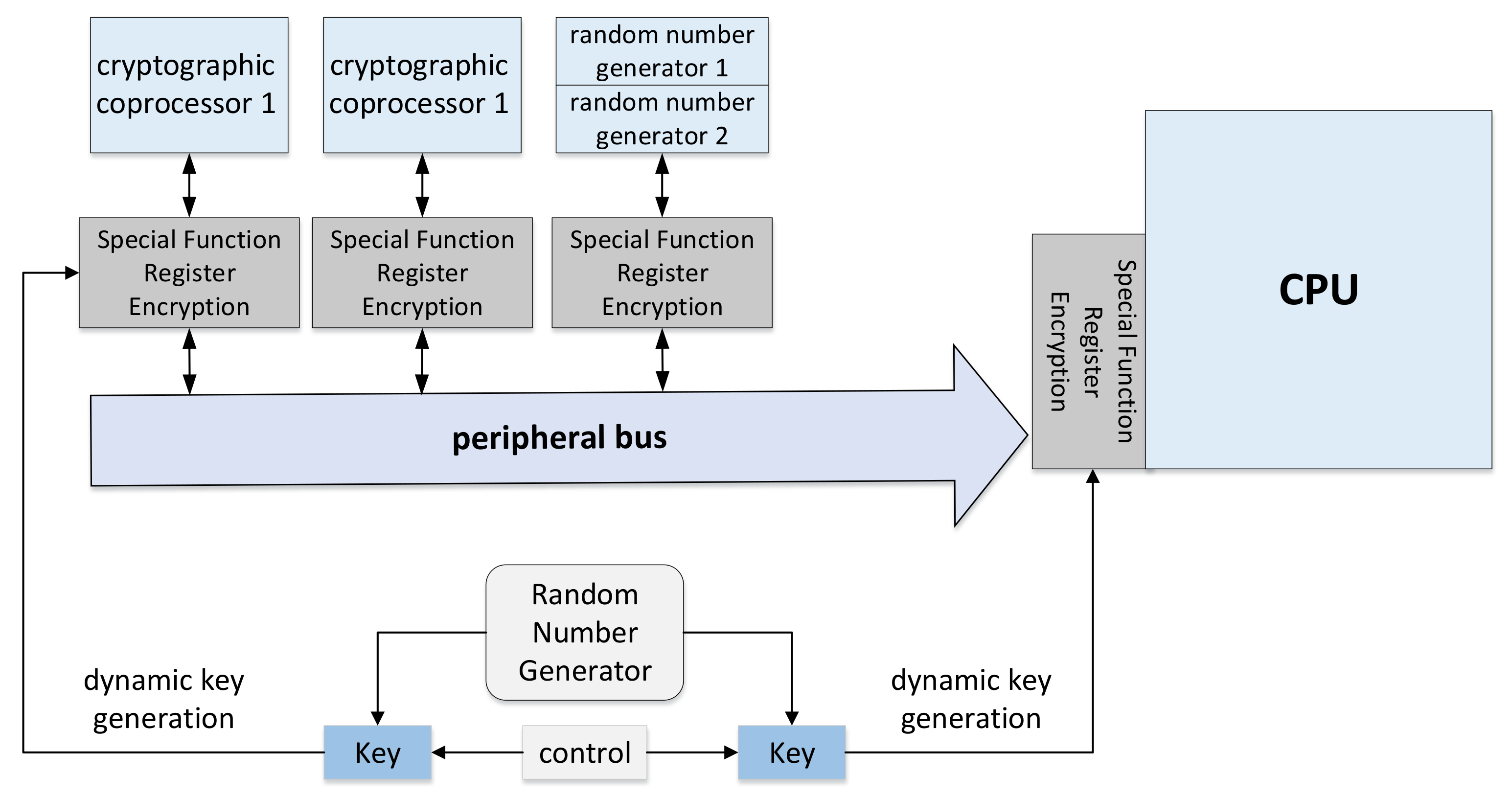
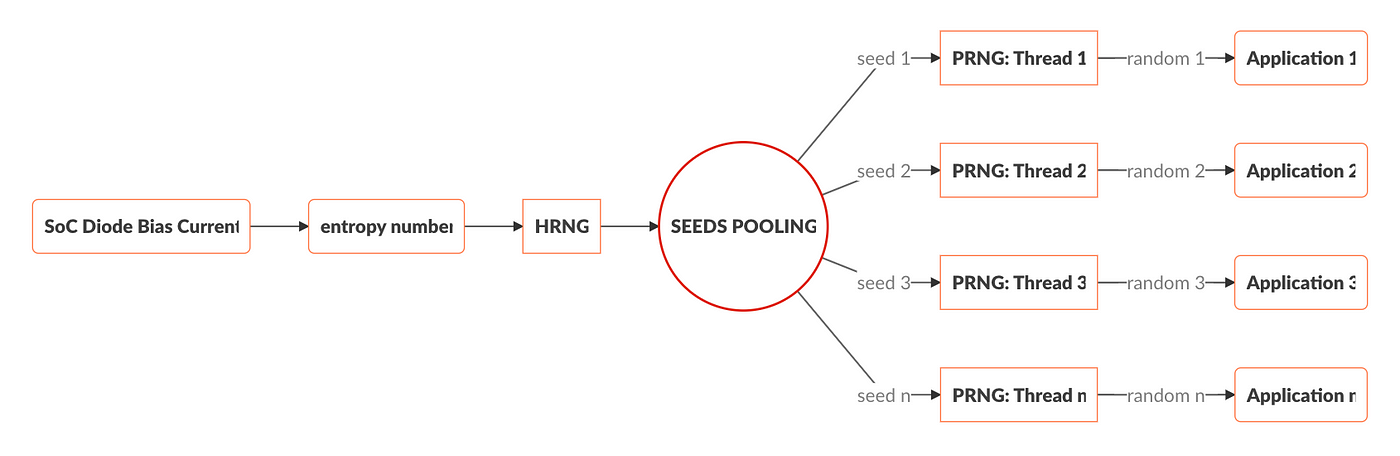
Entropy | Free Full-Text | Entropy Sources Based on Silicon Chips: True Random Number Generator and Physical Unclonable Function
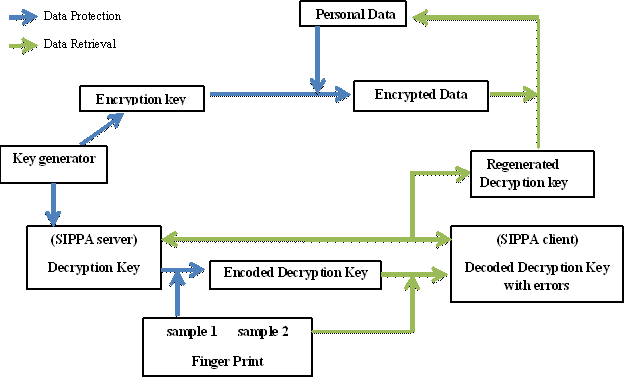
Generation of Cryptographic Keys from Personal Biometrics: An Illustration Based on Fingerprints | IntechOpen